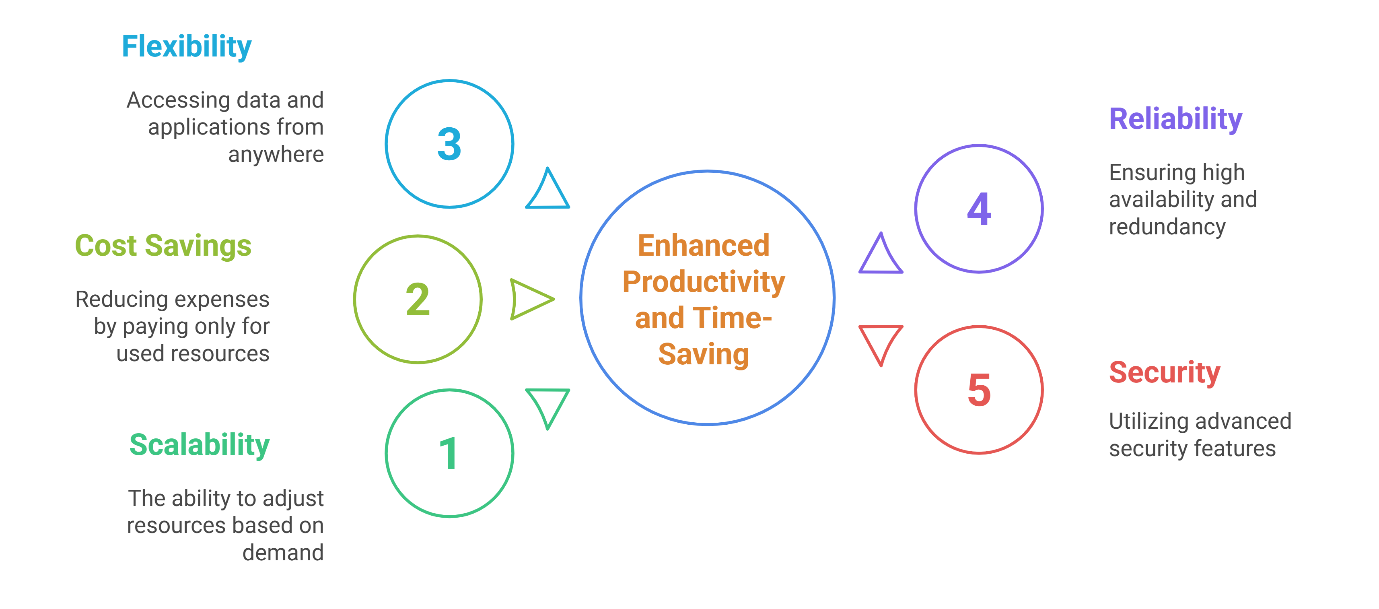
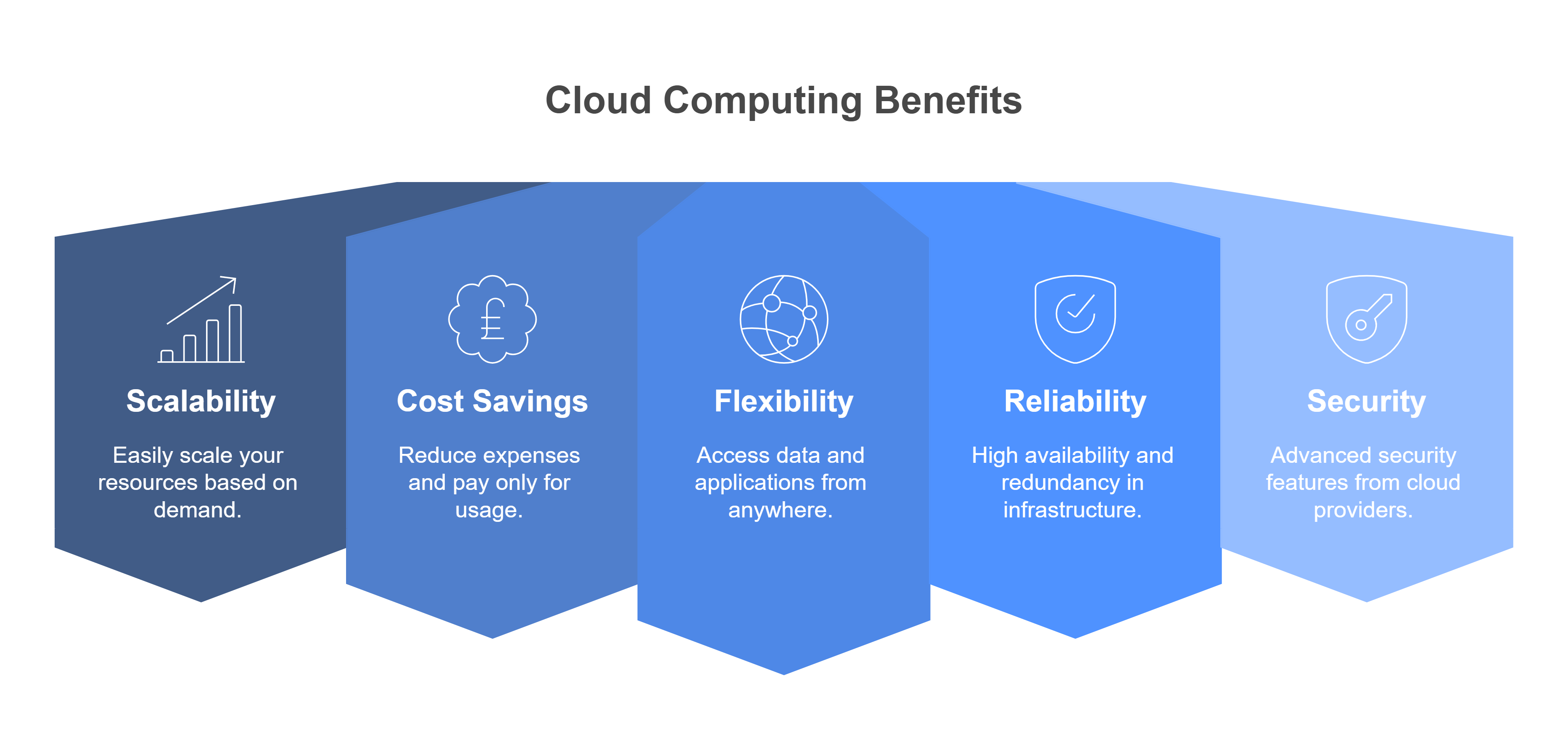
Cloud computing isn't just a buzzword; it's the backbone of modern, agile businesses. But let's be honest, wading through technical jargon can feel like navigating a storm. At Oasys Tech Solutions, we cut through the noise and deliver cloud solutions that make sense, empowering you to achieve more, securely.
Gartner predicts that by 2025, over half of enterprise IT spending will transition to the public cloud, highlighting the significance of Cloud computing in the digital landscape.
We help you develop a comprehensive cloud strategy that aligns with your business objectives. Our experts assess your current IT infrastructure and recommend the best cloud model and providers for your needs.
We manage the entire migration process, from planning to execution, ensuring a smooth transition with minimal disruption. Our team handles data migration, application deployment, and infrastructure setup in the cloud.
We analyze your cloud usage to identify areas for cost savings and performance improvements. Our optimization services include resource right-sizing, workload balancing, and cost management, leveraging advanced tools like containerization and microservices to maximize efficiency.
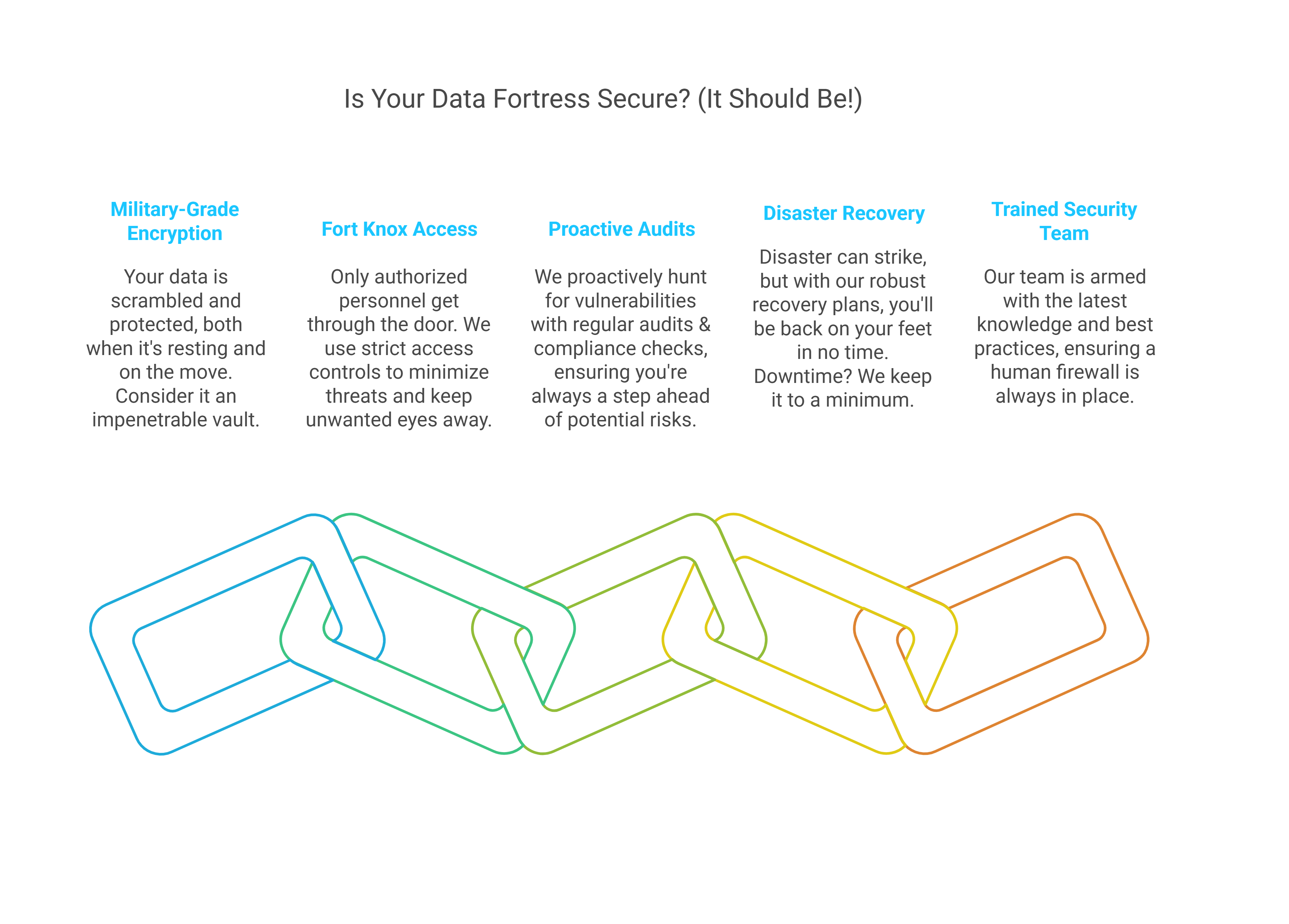
We implement robust security measures to protect your data and applications in the cloud. Our services cover identity and access management, encryption, and compliance with industry regulations.
We provide training sessions for your staff to get familiar with cloud technologies. Our support team is available to assist you with any issues or questions you have about your cloud environment.